News
We are stable!
Read more about it in our blog post.
New honeypot and proxy
New honeypot finally can handle all traffic. We have also space to scale even more now. New proxy is even more helping to use that new architecture on background but not mandatory to do upgrade.
For now we are still in beta phase to be sure it's stable but soon everything should be fixed and running smoothly.
New web and proxy
New web brings bug fixing, better structure of web with new design, possibility to use MojeID and public data available to download.
New proxy v1.3 brings bug fixing, possibility to change log level and support of not only RSA keys.
Improvements
Beta testing
What is a honeypot?
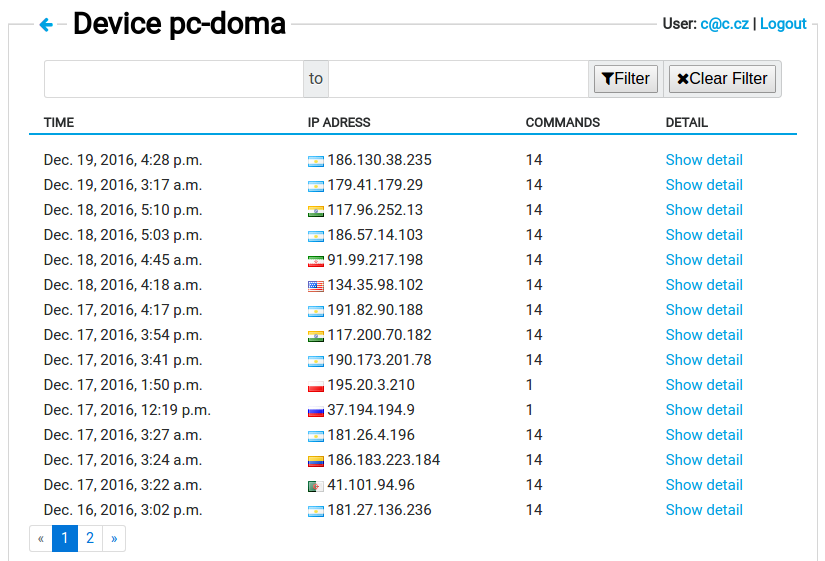
Honeypot is a special software which simulates an operating system and allows an attacker to log in via SSH or telnet and execute commands or download malware. Commands are recorded and used to analyze the behavior. Malware can be analyzed as well.
How does it work?
Volunteers interested in joining the research will register on this site and add the first device to get an identification token.
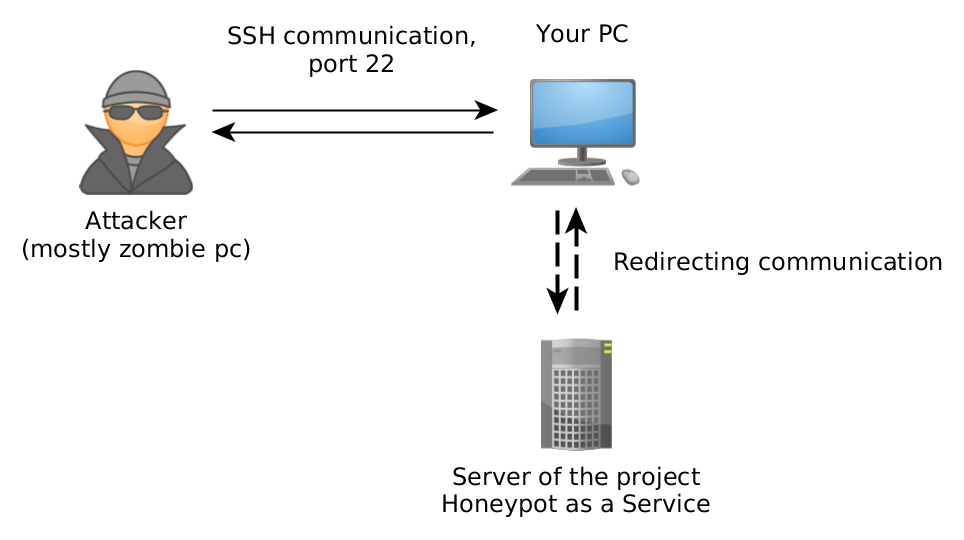
You install and run the HaaS proxy application, downloadable from our website, which forwards incoming traffic from port 22 (commonly used for SSH) to the HaaS server, where Cowrie honeypot simulates a device and records executed commands.
What do I get by joining the project?
- You will contribute to the improvement of cyber security and preparedness for cyber attacks in the Czech Republic.
- You will get interesting information about the attacks on your device.
How can I get involved?
Participation in the project is entirely voluntary. Just sign up, add a device and download and run the HaaS proxy application on your PC or server with Linux. In advance, thank you all for your participation in our research. You can find HaaS terms of use for download here.
How do we use the data?
Analyzing the behavior of attackers will be used for further innovation of mechanisms in SSH honeypot and for the National CSIRT of the Czech Republic - CSIRT.CZ.
Contact
Ask questions, report problems, or tell us your ideas via e-mail haas@nic.cz.